Dauthenticator
Dauthenticator is a decentralized version of the google authenticator app. Users can register entries and generate TOTP codes to authenticate against their favorite services and applications all over the world.
Project Description
Getting started
- Install Push Extension
To receive your OTP as a notification in the browser you must install and configure the Push extension (staging).
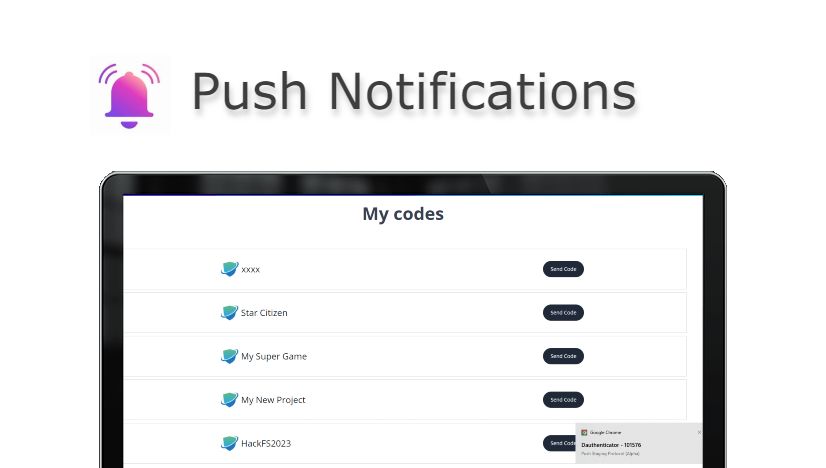
- Add Codes
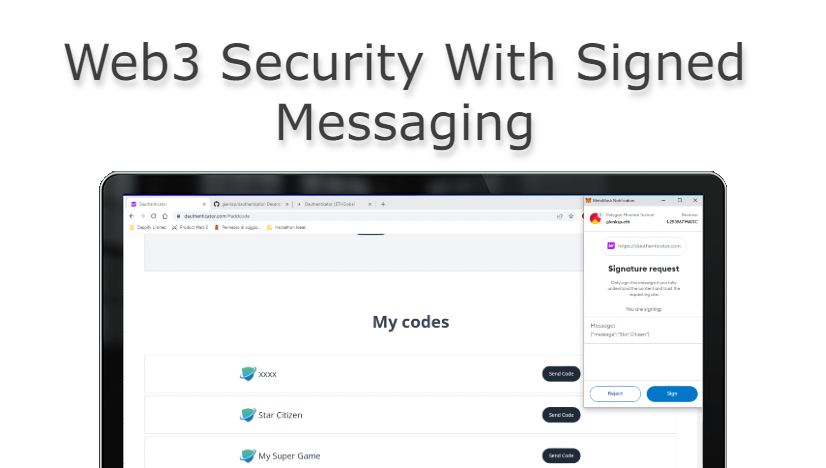
Connect your wallet and add your codes from any service for TOTP. These codes are stored with encryption.
- Generate OTP
Click Send Code. You will receive it via a browser notification through the Push Chrome extension.
Your codes are stored encrypted in an exclusive table in Tableland for your address and routed through a shared smart contract in Polygon Mumbai testnet.
How it's Made
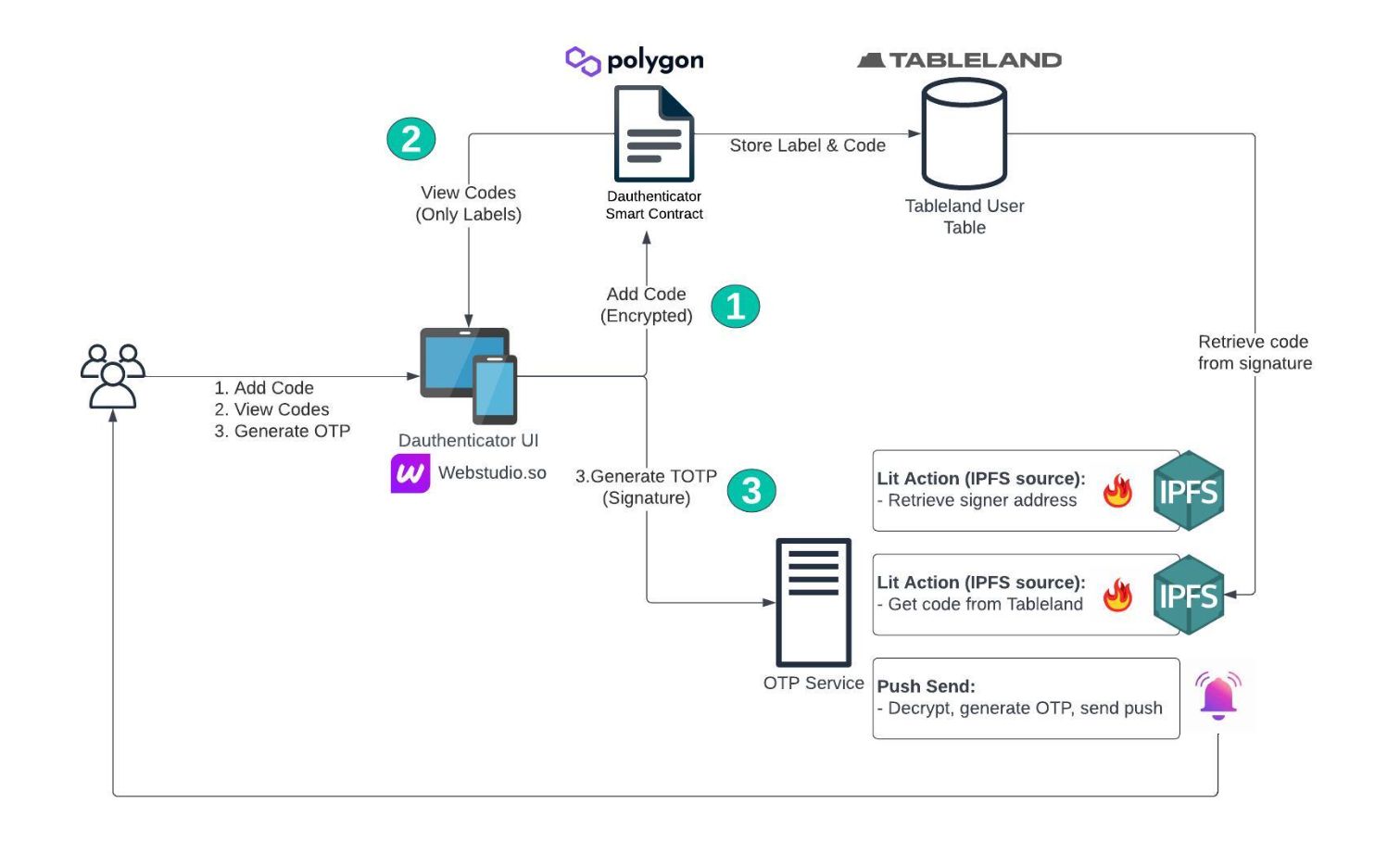
Architecture:
The three main actions include 1) the addition of new encrypted entries to a user table in Tableland and routed through the smart contract in Polygon. 2) The retrieval of the labels to display in the UI. 3) The user clicks on send code and signs such message including the label, this is processed by a containerized service that retrieves the signer, decrypts the code, and sends the push notification back to the requestor.
Pending (WIP):
- Encryption is not implemented yet!
- Retrieval of code from Lit Action is done against smart contract!
Technologies
A list of all the technologies used for the service. The frontend was created with webstudio.so, and the smart contract deployed to Polygon Mumbai.
- Webstudio.so:
The frontend was built with Webstudio, a no-code Web3 native drag and drop blocks platform powered by Tailwind. The application is deployed in IPFS with a custom domain.
- Lit Protocol
Two Lit Actions are deployed to IPFS and executed from a containerized service. One action unwraps the requestor signature, and the other retrieves the on-chain code to generate OTP.
- IPFS
Two Lit Actions source codes (Javascript) are hosted on IPFS and the CID references as the source of the action for computing on the OTP service. The frontend is hosted in IPFS as well.
- Tableland
From a smart contract indexer in Polygon (Mumbai), we create tables for each user and store their own credentials. Then retrieve the credentials from the OTP service via a signed message.
- Push Protocol
The OTP generated is sent to the requestor via Push Protocol. It requires the chrome extension (staging) installed. The user receives a browser notification with the OTP.
- Polygon
Polygon Mumbai testnet is the host of our smart contract that takes care of the indexing of users within the platform. This contract is queried from the UI and the OTP service.
This UI was built without writing code, using Webstudio.so!