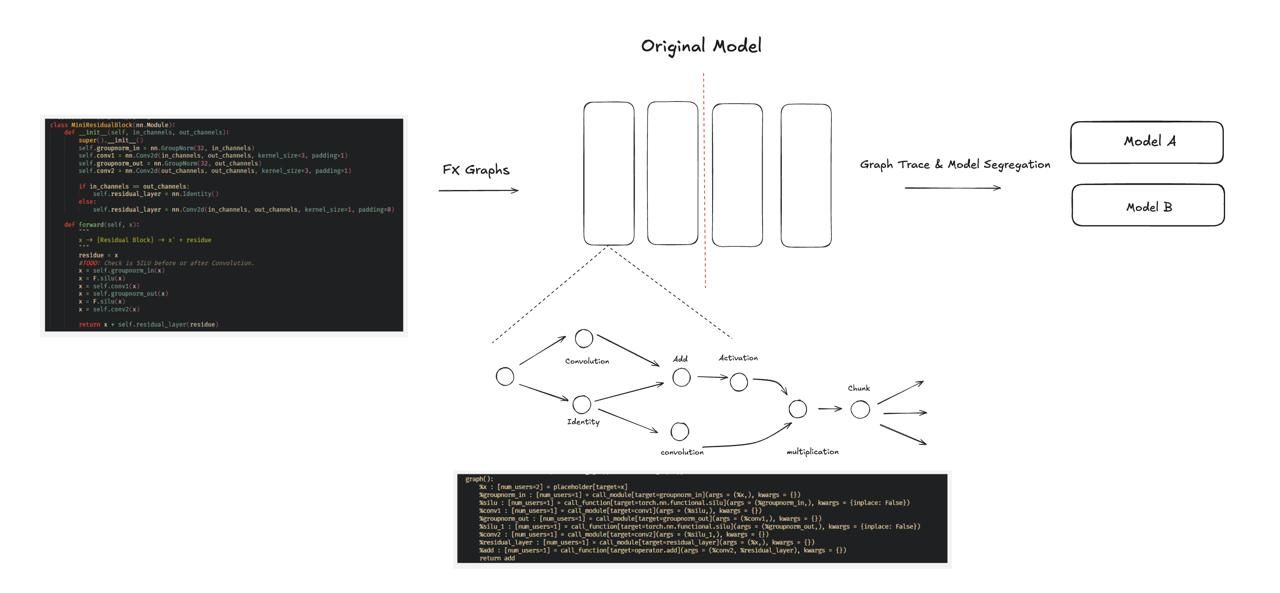
Encrypted_Compute
User's input is encrypted using FHE which he wants to run on an ML model. The initial layers of model are taken, and we perform operations of those initial layers on the encrypted data. Then the output is decrypted and sent to the model for further computation.
Project Description
Encrypted_Compute is an innovative platform designed to enable secure computations on private data using advanced computational models, such as machine learning models and large language models (LLMs), without exposing the data to model providers or any third parties. This solution is particularly crucial in fields where data privacy is paramount, such as healthcare, finance, and personal data analytics.
Problem Statement
Users often possess sensitive or private data that they cannot share publicly due to privacy concerns, legal restrictions, or personal preferences. Despite this, they may wish to leverage advanced computational models to gain insights, predictions, or analyses from their data. For instance, consider a patient suffering from a severe oral disease that results in distressing images. The patient wants to obtain a diagnosis or prognosis using AI models but is reluctant to share these images publicly or with model providers due to privacy concerns.
Solution Overview
Encrypted_Compute addresses this challenge by providing a secure platform where users can:
Encrypt their private data using Fully Homomorphic Encryption (FHE). Select and utilize computational models from various model creators. Specify initial layers of the model to perform computations on encrypted data. Ensure data remains confidential throughout the computation process. Receive results without ever exposing their raw data. Detailed Explanation
Data Encryption with Fully Homomorphic Encryption (FHE)
What is FHE?
Fully Homomorphic Encryption is an advanced cryptographic technique that allows computations to be performed directly on encrypted data without needing to decrypt it first. The result of these computations is also in encrypted form and, when decrypted, matches the outcome of operations performed on the plaintext data. User Data Encryption
Users upload their sensitive data (e.g., medical images) to the Encrypted_Compute platform. The platform encrypts the data using FHE algorithms, ensuring that the data remains secure and inaccessible to unauthorized parties, including the platform itself. Model Selection and Layer Specification
Model Repository
The platform hosts a repository of computational models uploaded by various model creators. These models can range from machine learning algorithms to complex neural networks and LLMs. User Choice and Customization
Users browse and select a model that suits their needs. Due to the computational intensity of performing operations on encrypted data, users can specify which initial layers of the model they want to run on their encrypted data. This partitioning is essential because processing the entire model on encrypted data is currently impractical due to computational limitations. Secure Computation in a Trusted Execution Environment (TEE)
What is a TEE?
A Trusted Execution Environment is a secure area within a processor that ensures code and data loaded inside are protected with respect to confidentiality and integrity. TEEs prevent unauthorized access and tampering while code is executing within them. Utilizing Phala Network
The Encrypted_Compute platform leverages the Phala Network, which provides decentralized TEE services. Phala Network allows computations to be performed in a secure and private manner, ensuring that the encrypted data remains confidential. Computational Constraints
Phala Network's TEE services have a time limit, typically around 1 minute. This limitation necessitates efficient computation and is another reason for processing only the initial layers of the model within the TEE. Intermediate Output Decryption and Obfuscation
Decrypting the Output
After the computation within the TEE, the resulting output (still encrypted) is decrypted by the platform. This output is an intermediate representation of the data after being processed by the initial model layers. Obfuscated Data
The decrypted output is obfuscated, meaning it is transformed in a way that retains essential features needed for further computation but does not reveal the original sensitive data. Obfuscation ensures that even if the data is intercepted or accessed by unauthorized parties, the original information cannot be reconstructed. Final Computation by Model Creator
Transferring Obfuscated Data
The obfuscated intermediate data is securely transferred to the model creator. The model creator processes this data through the remaining layers of their model. Data Privacy Assurance
The model creator does not have access to the user's raw data at any point. The obfuscated data is designed to prevent reverse-engineering or reconstruction of the original data. Result Delivery to User
Receiving the Final Output
The model creator sends the final computation results back to the Encrypted_Compute platform. The platform then delivers these results to the user. Confidentiality Maintained
Throughout the entire process, the user's data remains confidential. The user obtains the desired output without compromising their privacy. Advantages of Encrypted_Compute
Enhanced Data Privacy
Users can utilize advanced computational models without exposing their sensitive data. The combination of FHE and TEE technologies ensures end-to-end data confidentiality. Flexibility and Control
Users can choose which parts of the model to run on their data. This allows for customization based on computational constraints and privacy preferences. Secure Collaboration
Model creators can offer their services without risking exposure to sensitive data. Encourages more widespread adoption of AI and ML models in sensitive fields. Scalability
The platform can be expanded to include more models and support a larger user base. Modular design allows for integration with various computational models and services. Technical Components Explained
Fully Homomorphic Encryption (FHE)
Functionality
Allows for arbitrary computation on encrypted data. Ensures that the data remains encrypted throughout the computation process. Challenges
Computationally intensive and slower than operations on plaintext data. Requires optimization and efficient algorithms to be practical for real-world applications. Trusted Execution Environment (TEE)
Functionality
Provides a secure enclave for computations. Protects data and code from external access and tampering. Phala Network Integration
Offers decentralized TEE services suitable for the platform's needs. Time-limited computations necessitate efficient processing strategies. Model Partitioning
Why Partition Models?
Running entire models on encrypted data is impractical due to computational overhead. Partitioning allows initial layers (e.g., feature extraction layers) to run on encrypted data, reducing computational demands. Benefits
Balances between data privacy and computational feasibility. Enables the processing of complex models within the constraints of FHE and TEE. Obfuscated Intermediate Data
Purpose
Acts as a bridge between the encrypted computation and the model creator's processing. Contains necessary features extracted from the data without revealing sensitive information. Security Measures
Designed to prevent reverse-engineering. Ensures that even if accessed, the original data cannot be reconstructed. Use Case Scenario
Healthcare Application Patient Uploads Data A patient uploads encrypted medical images to the platform. Model Selection The patient selects a diagnostic AI model and specifies the initial layers for encrypted computation. Secure Computation The encrypted images are processed within the TEE, extracting essential features. Data Obfuscation The intermediate output is decrypted and obfuscated. Model Creator Processing The obfuscated data is sent to the model creator, who processes it through the remaining model layers. Receiving Results The patient receives a diagnosis or analysis without ever exposing their raw images. Challenges and Considerations
Computational Overhead
FHE is resource-intensive, leading to longer computation times. Requires powerful hardware and optimization techniques. Time Constraints
The 1-minute limit within the TEE necessitates efficient algorithms and model partitioning. Complex models may need further segmentation or approximation methods. Model Compatibility
Not all models are suitable for partitioning or encrypted computation. Collaboration with model creators is essential to adapt models for the platform. Security Assurance
Continuous updates and audits are necessary to maintain security. Potential vulnerabilities in encryption or TEE implementation must be addressed promptly. Future Enhancements
Optimizing FHE Algorithms
Research into more efficient FHE schemes could reduce computational overhead. Implementation of hybrid encryption methods to balance performance and security. Extending TEE Capabilities
Exploring partnerships with other TEE providers to extend computation time limits. Developing proprietary TEE solutions tailored to the platform's needs. Model Repository Expansion
Encouraging more model creators to join the platform. Providing tools and guidelines for model adaptation and partitioning. User Interface Improvements
Enhancing the platform's usability with intuitive design. Providing detailed documentation and support for users and model creators. Conclusion
Encrypted_Compute offers a groundbreaking solution to the challenge of performing computations on sensitive data without compromising privacy. By integrating advanced cryptographic techniques like FHE with secure computation environments like TEE, the platform enables users to harness the power of advanced models while maintaining full control over their data. This approach not only benefits individual users but also has the potential to transform industries where data privacy is a critical concern.
Key Takeaways
Data Privacy and Security
Users retain control over their data throughout the entire process. Advanced encryption and secure computation environments safeguard against unauthorized access. Empowering Users
Provides access to cutting-edge computational models without sacrificing privacy. Enables users to make informed decisions based on advanced analytics. Innovative Collaboration
Bridges the gap between data owners and model creators. Fosters a secure ecosystem for sharing and processing sensitive information.
How it's Made
Detailed Explanation
Data Encryption with Fully Homomorphic Encryption (FHE)
What is FHE?
Fully Homomorphic Encryption is an advanced cryptographic technique that allows computations to be performed directly on encrypted data without needing to decrypt it first. The result of these computations is also in encrypted form and, when decrypted, matches the outcome of operations performed on the plaintext data. User Data Encryption
Users upload their sensitive data (e.g., medical images) to the Encrypted_Compute platform. The platform encrypts the data using FHE algorithms, ensuring that the data remains secure and inaccessible to unauthorized parties, including the platform itself. Model Selection and Layer Specification
Model Repository
The platform hosts a repository of computational models uploaded by various model creators. These models can range from machine learning algorithms to complex neural networks and LLMs. User Choice and Customization
Users browse and select a model that suits their needs. Due to the computational intensity of performing operations on encrypted data, users can specify which initial layers of the model they want to run on their encrypted data. This partitioning is essential because processing the entire model on encrypted data is currently impractical due to computational limitations. Secure Computation in a Trusted Execution Environment (TEE)
What is a TEE?
A Trusted Execution Environment is a secure area within a processor that ensures code and data loaded inside are protected with respect to confidentiality and integrity. TEEs prevent unauthorized access and tampering while code is executing within them. Utilizing Phala Network
The Encrypted_Compute platform leverages the Phala Network, which provides decentralized TEE services. Phala Network allows computations to be performed in a secure and private manner, ensuring that the encrypted data remains confidential. Computational Constraints
Phala Network's TEE services have a time limit, typically around 1 minute. This limitation necessitates efficient computation and is another reason for processing only the initial layers of the model within the TEE. Intermediate Output Decryption and Obfuscation
Decrypting the Output
After the computation within the TEE, the resulting output (still encrypted) is decrypted by the platform. This output is an intermediate representation of the data after being processed by the initial model layers. Obfuscated Data
The decrypted output is obfuscated, meaning it is transformed in a way that retains essential features needed for further computation but does not reveal the original sensitive data. Obfuscation ensures that even if the data is intercepted or accessed by unauthorized parties, the original information cannot be reconstructed. Final Computation by Model Creator
Transferring Obfuscated Data
The obfuscated intermediate data is securely transferred to the model creator. The model creator processes this data through the remaining layers of their model. Data Privacy Assurance
The model creator does not have access to the user's raw data at any point. The obfuscated data is designed to prevent reverse-engineering or reconstruction of the original data. Result Delivery to User
Receiving the Final Output
The model creator sends the final computation results back to the Encrypted_Compute platform. The platform then delivers these results to the user. Confidentiality Maintained
Throughout the entire process, the user's data remains confidential. The user obtains the desired output without compromising their privacy. Advantages of Encrypted_Compute
Enhanced Data Privacy
Users can utilize advanced computational models without exposing their sensitive data. The combination of FHE and TEE technologies ensures end-to-end data confidentiality. Flexibility and Control
Users can choose which parts of the model to run on their data. This allows for customization based on computational constraints and privacy preferences. Secure Collaboration
Model creators can offer their services without risking exposure to sensitive data. Encourages more widespread adoption of AI and ML models in sensitive fields. Scalability
The platform can be expanded to include more models and support a larger user base. Modular design allows for integration with various computational models and services.