HackTrace
Our app could be a key resource for the crypto community, providing features like hack report submission, blacklisting malicious addresses, and real-time alerts to prevent exploits. It offers intelligence and support to victims and on-chain detectives..
Project Description
Our app could be a vital asset for the crypto community, blending security with support. It allows users to report hack incidents in detail, helping to understand and prevent similar threats. A standout feature is the conditional blacklisting of suspicious addresses, which actively blocks malicious actors and protects user assets (will be available in future versions)
Real-time alerts, based on advanced pattern analysis, are crucial for stopping further exploitation after a breach. These alerts enable users to quickly respond to emerging threats. (will be available in future versions)
Beyond just technical safeguards, our platform builds a supportive environment. Victims of hacks receive actionable intelligence and community support, turning individual experiences into collective wisdom for better risk management (through the PUSH chats, will be available in future versions)
How it's Made
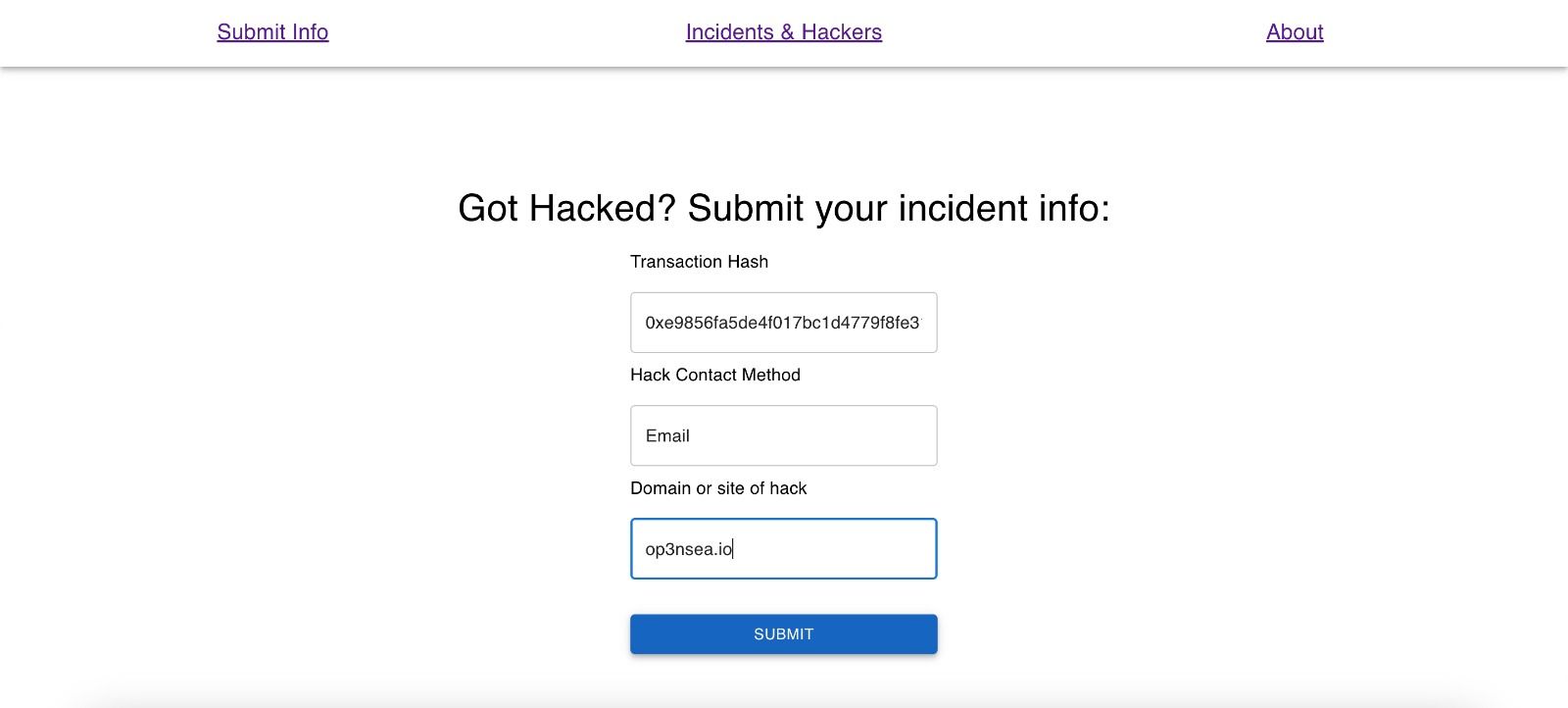
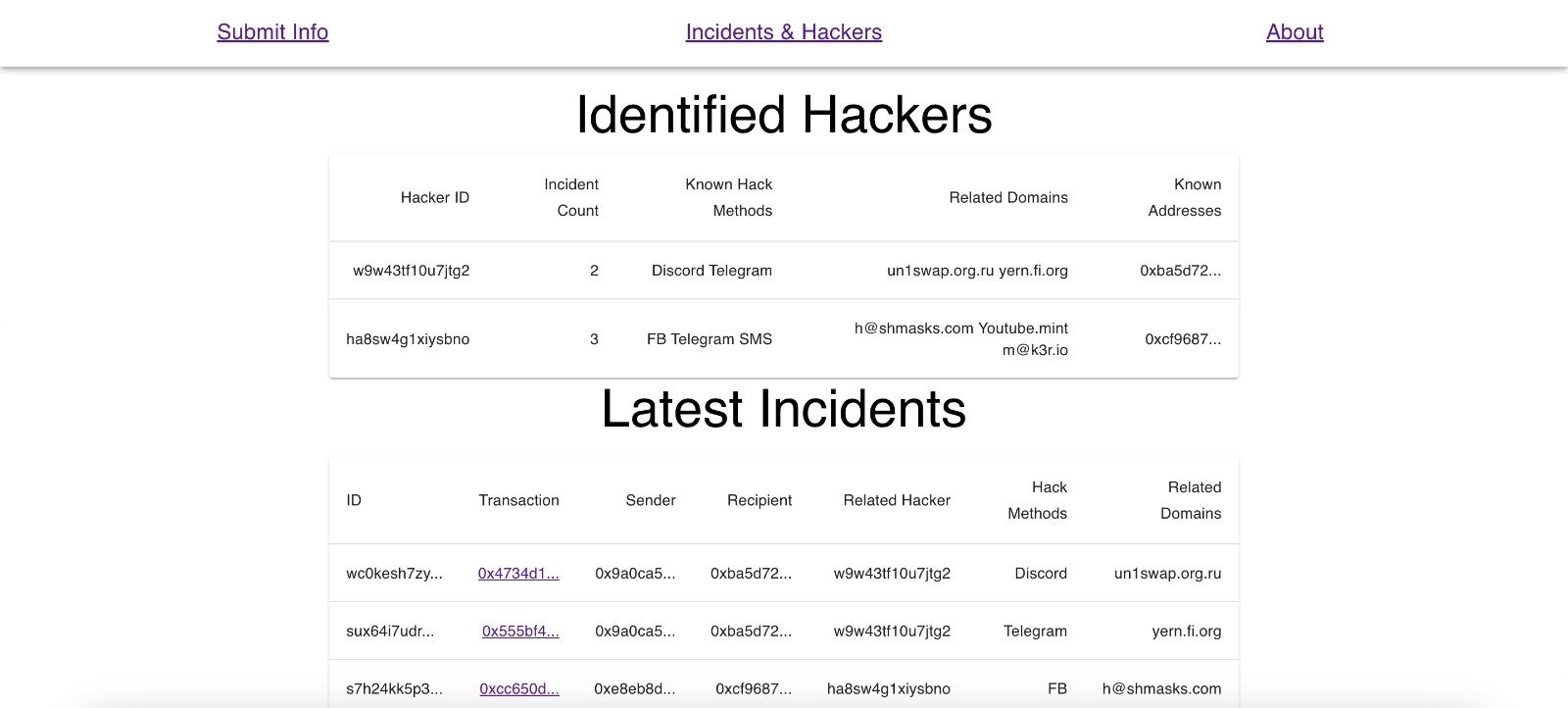
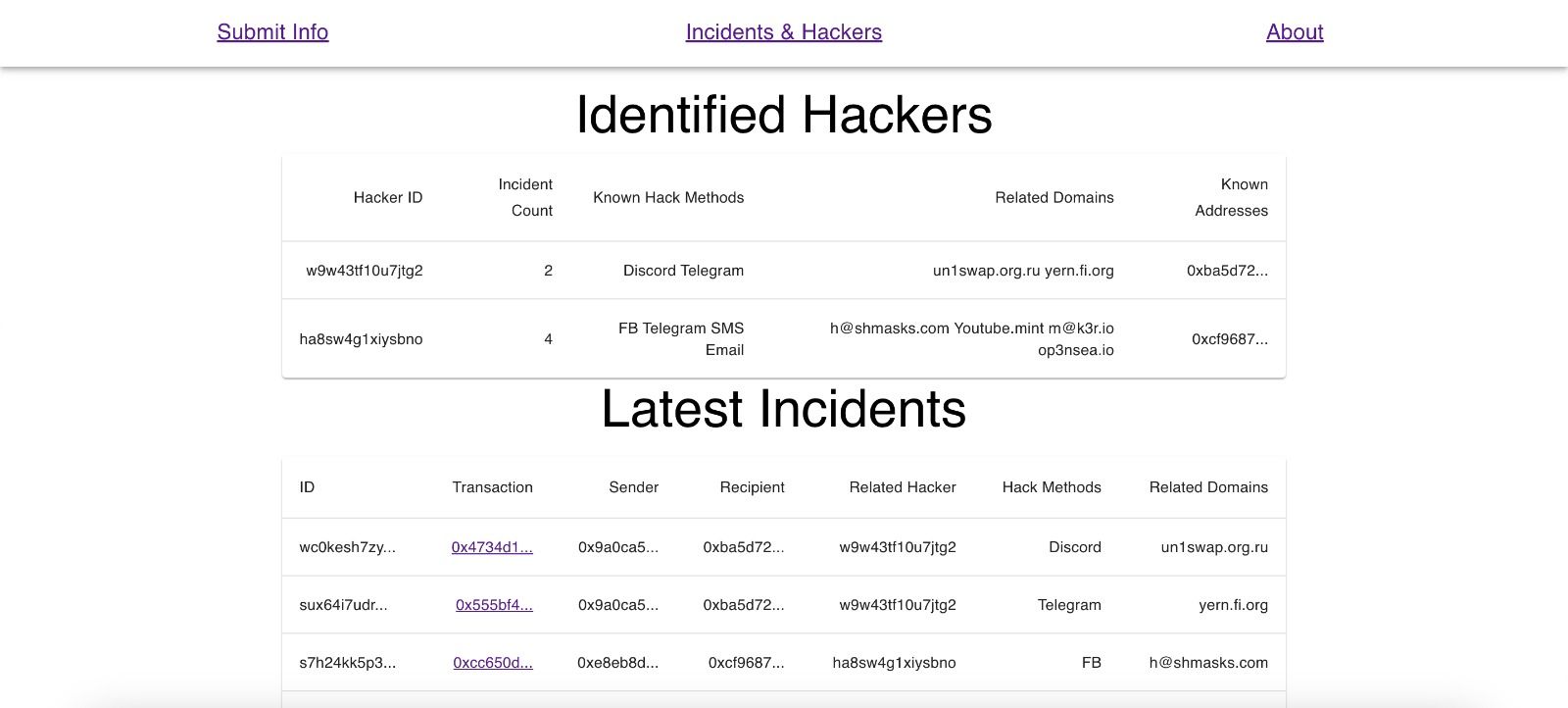
Our project is made almost entirely in JavaScript, particularly React. For the backend, we use a simple pocketbase database that runs alongside the server. While the project doesn't utilize smart contracts, it makes heavy use of known data structures and concepts in the EVM, specifically with transactions. When users visit the website, they are requested to submit the transaction when the hack occurred (that is the assets are moved), how did the hacker got the funds (method of communication such as discord or telegram), and finally any suspicious domain names that were used to actually submit the seed phrase/sign a malicious contract. The latter two represent the link to the web2 world that is crucial in security and lets law enforcement find the hackers, as this is often where they have holes in their plans. Upon receipt of this information, the app performs an API call to the BlockCypher API to get some additional information about the transaction, such as the sender and the recipient. The latter is particularly useful to identify (and verify) the potential hacker address. If the existing hacker database has a match for the receiving address, the hacker profile is updated with all this information such as the domains they have used, the method of hacking, and of course the count of incidents they have been involved with. That way, the hacker has that much more known about them publicly, potentially bringing them to justice faster. It is at this point that we intended to use PUSH protocol to notify other victims that are subscribed to this hacker's "channel" so that they can both rest easier knowing that more is known about the hacker, and also see if there are any other details they may add.