Sapien
🔐 Sapiens: omnichain identity verification leveraging zero knowledge machine learning. Say goodbye to invasive proof of humanity methods and stay protected from sybil attacks!
Project Description
Proof of humanity is essential to confirm that a human, rather than a bot or automated system, is responsible for a particular action. This helps prevent fraud, abuse, and other malicious activities that can be carried out by non-human entities. However, some current approaches require users to divulge more information publicly than necessary. For example, proof of humanity asks users to upload their video, which can be seen by anyone.
Introducing Sapien
Sapien is a decentralized identity platform that seamlessly associates a human identity with a blockchain address without revealing any sensitive information. Sapien addresses several critical challenges faced by traditional identity systems and existing blockchain-based identity solutions.
Key Advantages:
- Mitigation of Sybil Attacks: Sapien employs ZKML to do off-chain authentication of human face and posts the proof on-chain for verification. The method ensures a human identity behind an address through cryptographic security. Sybil attacks occur when a single user creates multiple identities to manipulate or exploit a system. By linking each human identity to a unique blockchain address, Sapien ensures that one person is represented by only one verifiable identity, safeguarding the integrity of the platform.
- Soul Bound Tokens: These tokens are intricately linked to a verified human identity and cannot be transferred to another individual. They can only be transferred to another address linked to the same human identity. This unique feature opens up new possibilities in features like GitPOAP which can allow the current non-transferrable credential to be transferable between addresses linked to same human identity.
- Decentralized KYC (Know Your Customer): One of the most significant advantages of Sapien is its ability to facilitate decentralized KYC processes. Traditional KYC methods often involve sharing sensitive personal information with centralized authorities, raising concerns about data privacy and security.
- Privacy-Centric Authentication: Unlike existing solutions that might compromise user privacy by requesting authentication videos or other intrusive data, Sapien focuses on privacy-centric authentication methods. The platform employs ZK protocols to validate human identity without compromising sensitive information. This ensures that users have peace of mind knowing that their data remains secure and protected.
How it's Made
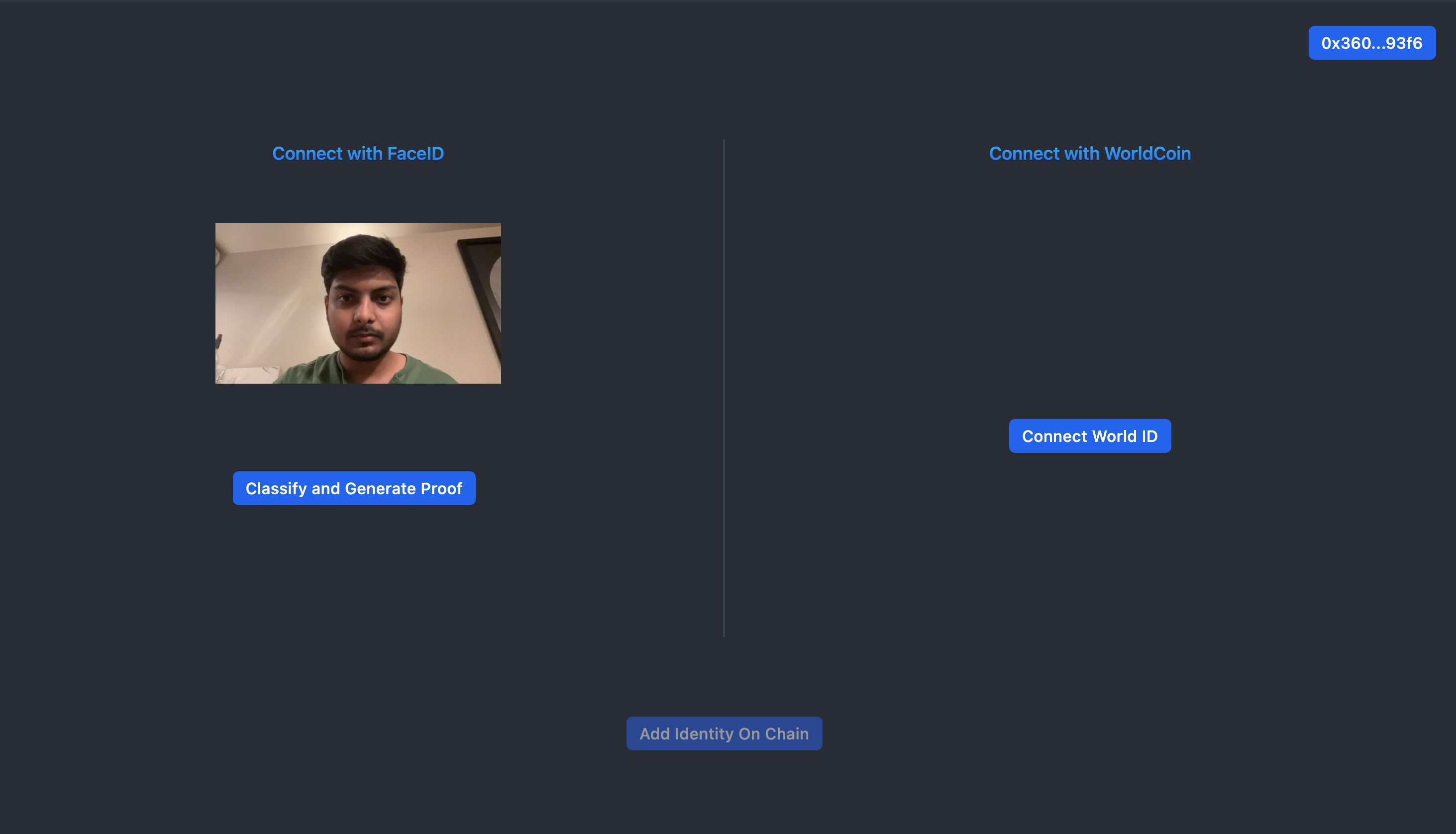
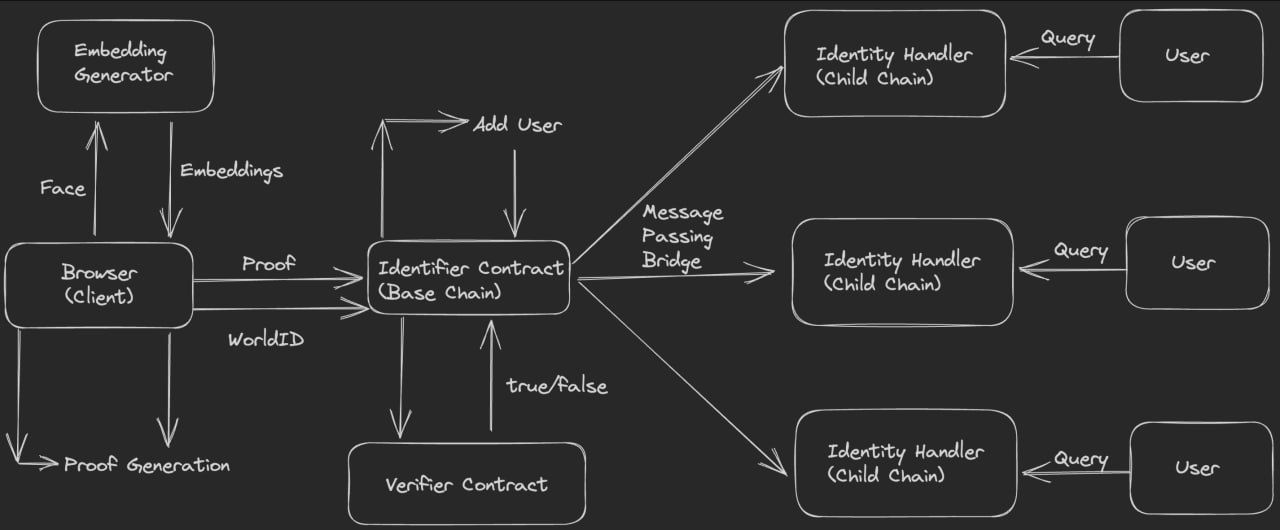
- To establish a universal proof of human identity, users need to authenticate themselves with their face or their iris. However, running Machine Learning models for facial classification on-chain is too expensive due to gas constraints. As a solution, we generate a proof of inference off-chain, which is then posted and verified on-chain. This verification process takes constant time, making it a suitable computation for on-chain execution.
- For the face-based authentication system, the machine learning model we use for inference comprises two components. The first is a server that produces facial embeddings from an image. The second component is a classifier that uses these embeddings to distinguish between human identities.
- After generating a proof on the browser, the client posts it on-chain via the frontend. The smart contract is then responsible for calling the verifier contract to validate the proof and add the user to our protocol. Once the user is verified, they can associate an address with their identity.
- For iri-based authentication system, users can use WorldID to create a universal ID within our system.
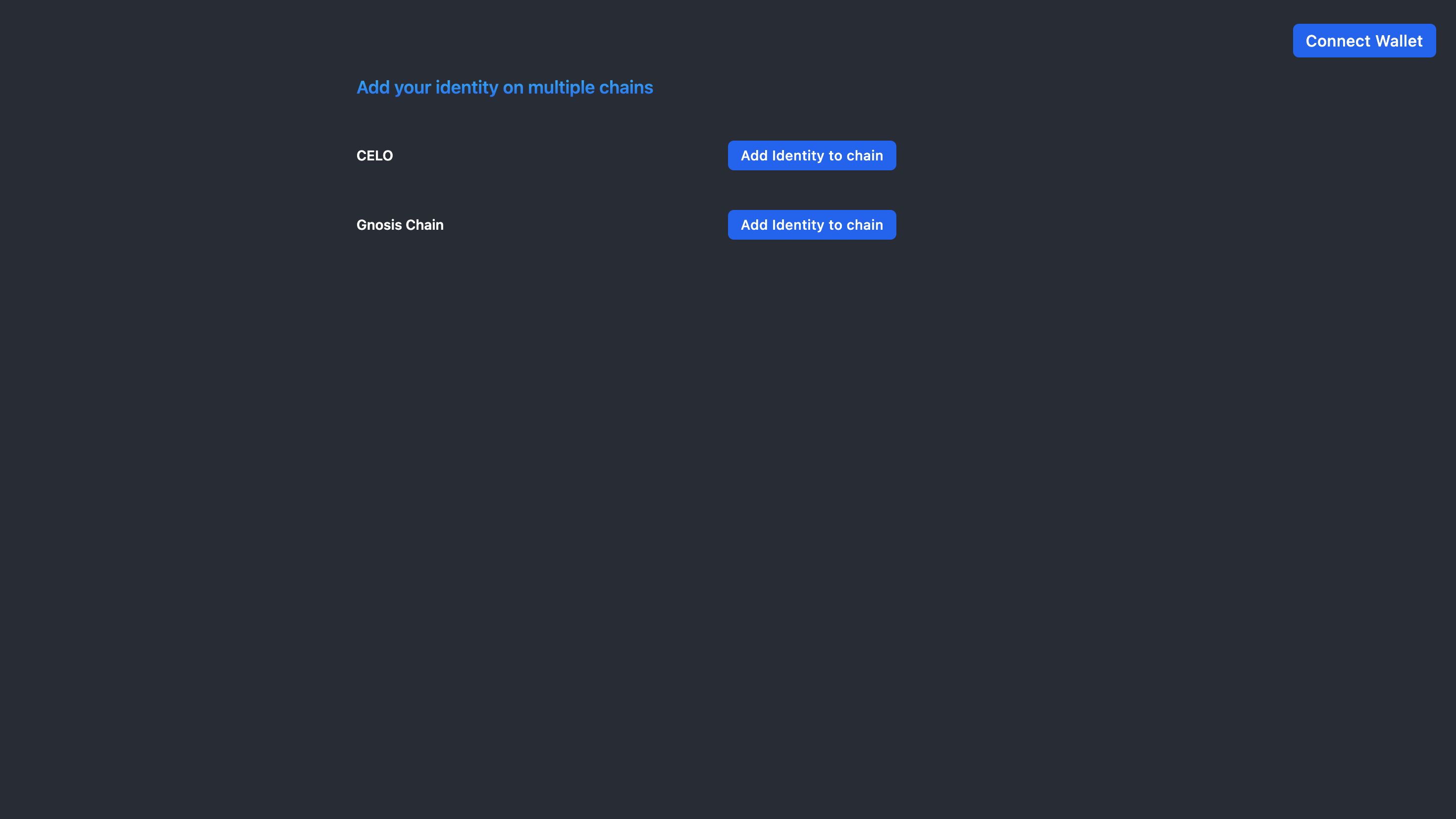
- Users also have the option to use their identity on other chains. We use message passing to relay the saved identity on the base chain and propagate it to child chains. For this, we are using the HyperLane bridge for message passing.
- The user can authenticate with any DApp that supports the protocol on any of the chains, including both child chains and the base chain.