Secure Social Swap
Secure Social Swap allows users to monetize their web2.0 social credentials by buying and selling their accounts.
Project Description
Current account trading platforms like g2g.com and playerauctions.com require you to trust the platform to mediate the trades. With Secure Social Swap, it is done in a decentralized way through smart contracts. 0 Trust required.
We believe users should have sovereignty over their data. People should own their digital presence and feel free to sell any assets they have acquired, whether it be followers or weapon unlocks.
Selling your web2.0 social account may violate some terms of service, but it is not illegal to sell your youtube, twitter, or steam account.
How it's Made
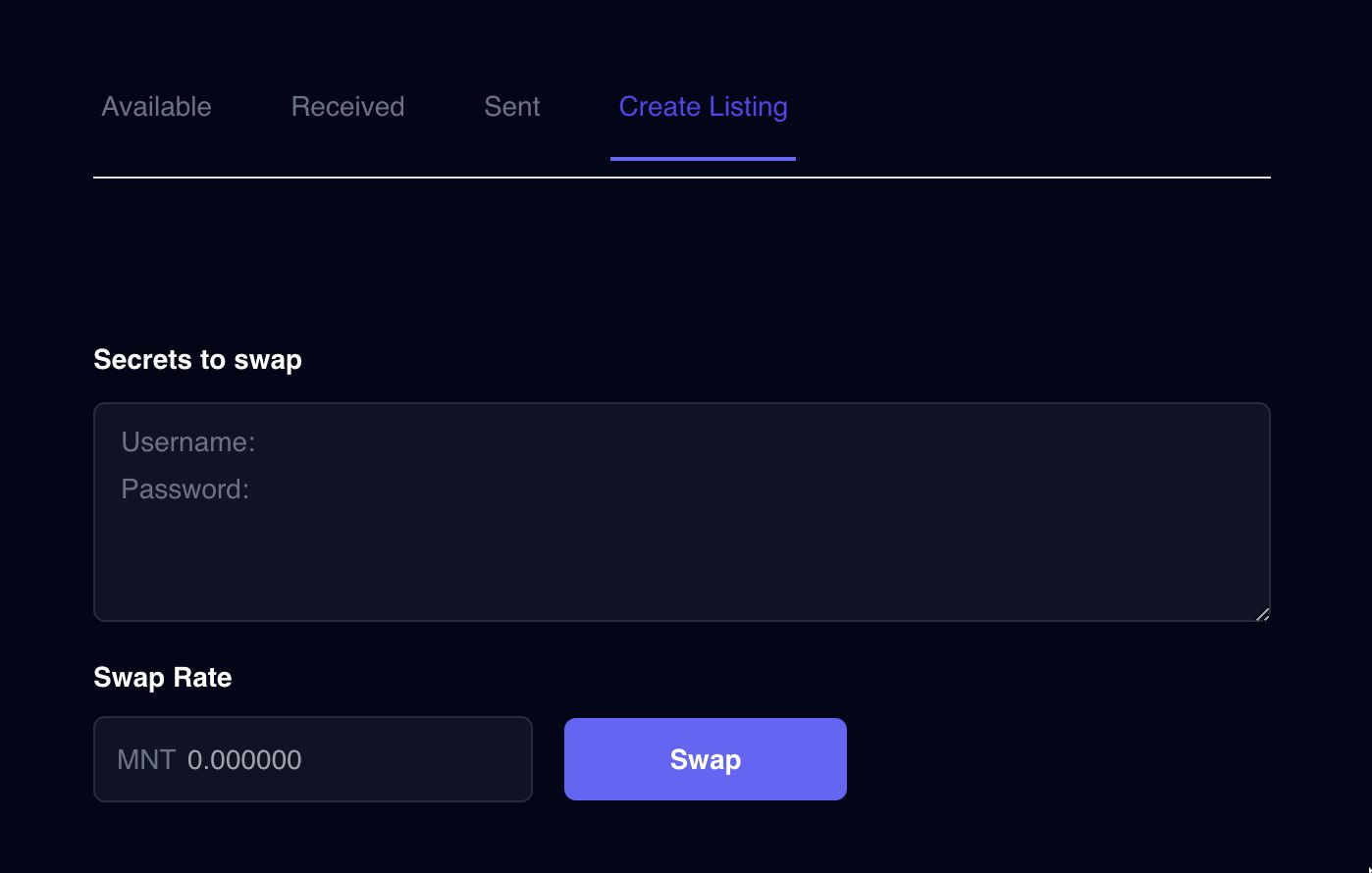
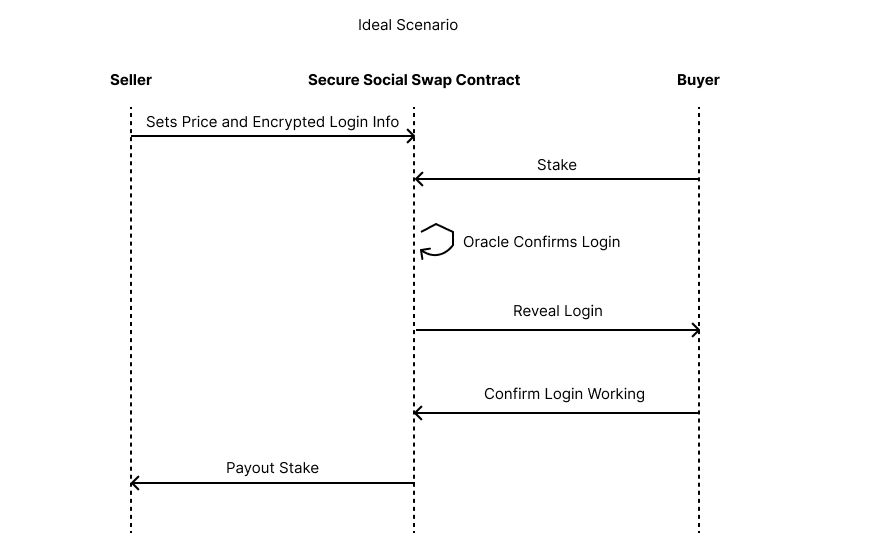
- When a user lists their account, a contract is deployed where the listing price is set and their encrypted login credentials are stored.
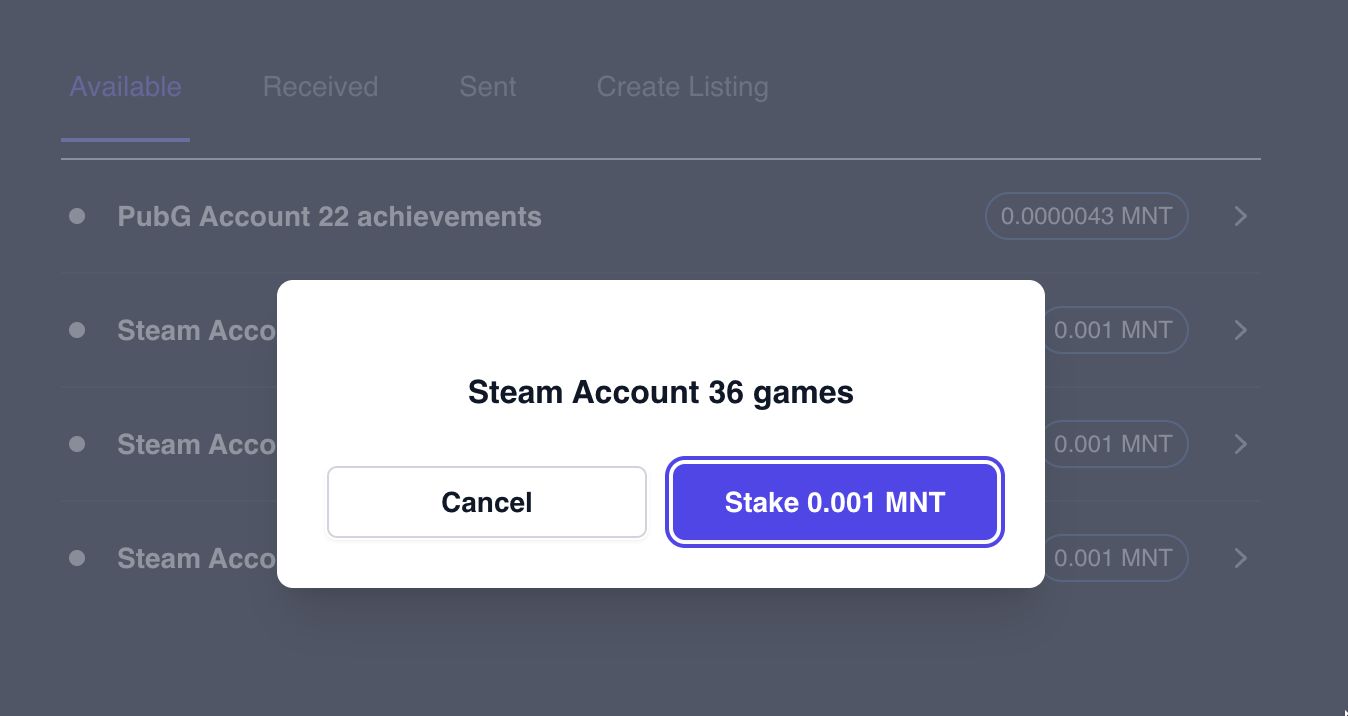
- A buyer stakes the set price onto the contract, for insurance.
- An oracle calls an endpoint we created to verify the login credentials work
- Buyer address is set to be allowed to decrypt login credentials
- Encrypted login info is provided to buyer, where they decrypt
- Buyer tests login info and confirms or denies on the contract
- Stake is paid out to seller
- Seller is notified of their sale
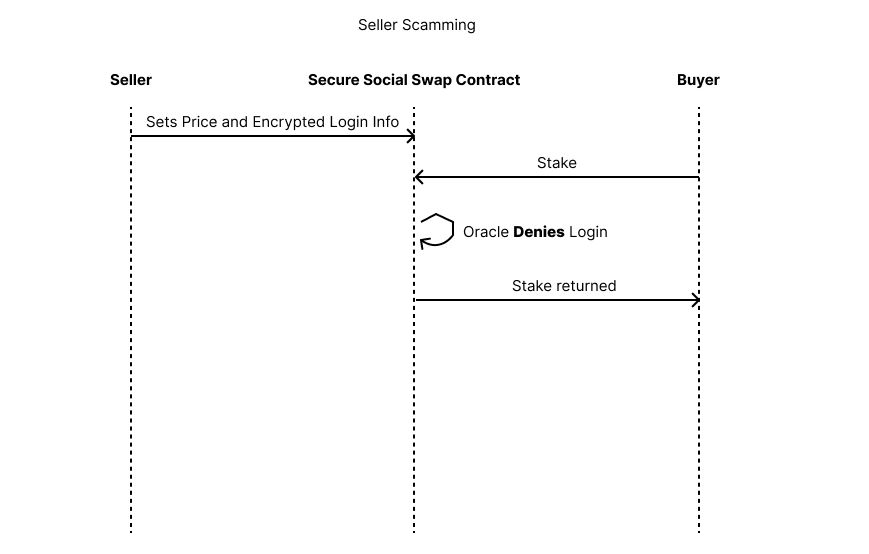
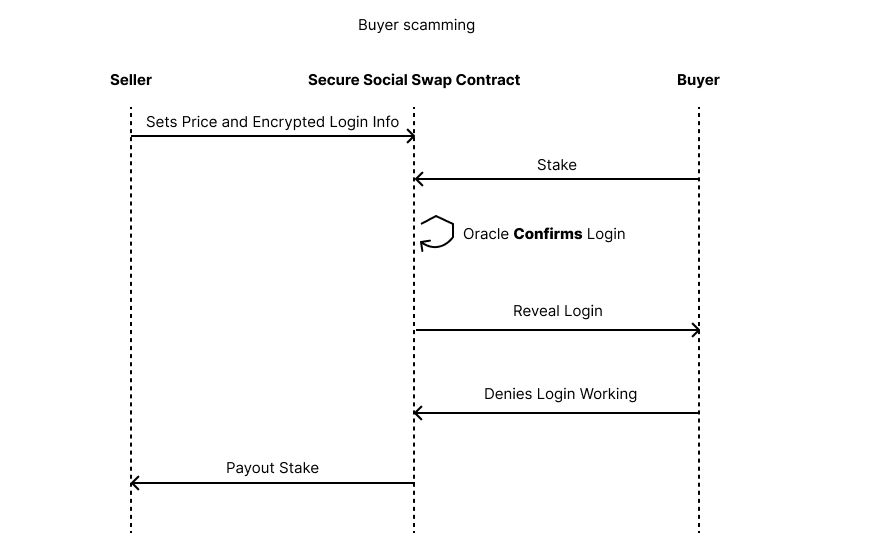
If a seller sends bad login credentials, our oracle will deny it and stake is returned to buyer. If a buyer claims login doesn't work, but our oracle confirmed the login, the stake is paid out to buyer. This prevents scamming from both parties with no need for an intermediary.
Future considerations we have are:
- ZK Proofs and Attestations for successful transfer of credentials, as well as verification that user owns credentials.
- Login Rentals. Could be facilitated via NFTs that allow the encryption/decryption of the login credentials.
Tech used: Vite, Solidity, Ethers, Threshold, Push Protocol