SIREN
SIREN, a new Slither plugin that creates sequence diagrams for smart contracts! Protocols are becoming increasingly complex, making it hard to assess for vulnerabilities/critical errors. Generate flow visualizations that help you validate your contract logic!
Project Description
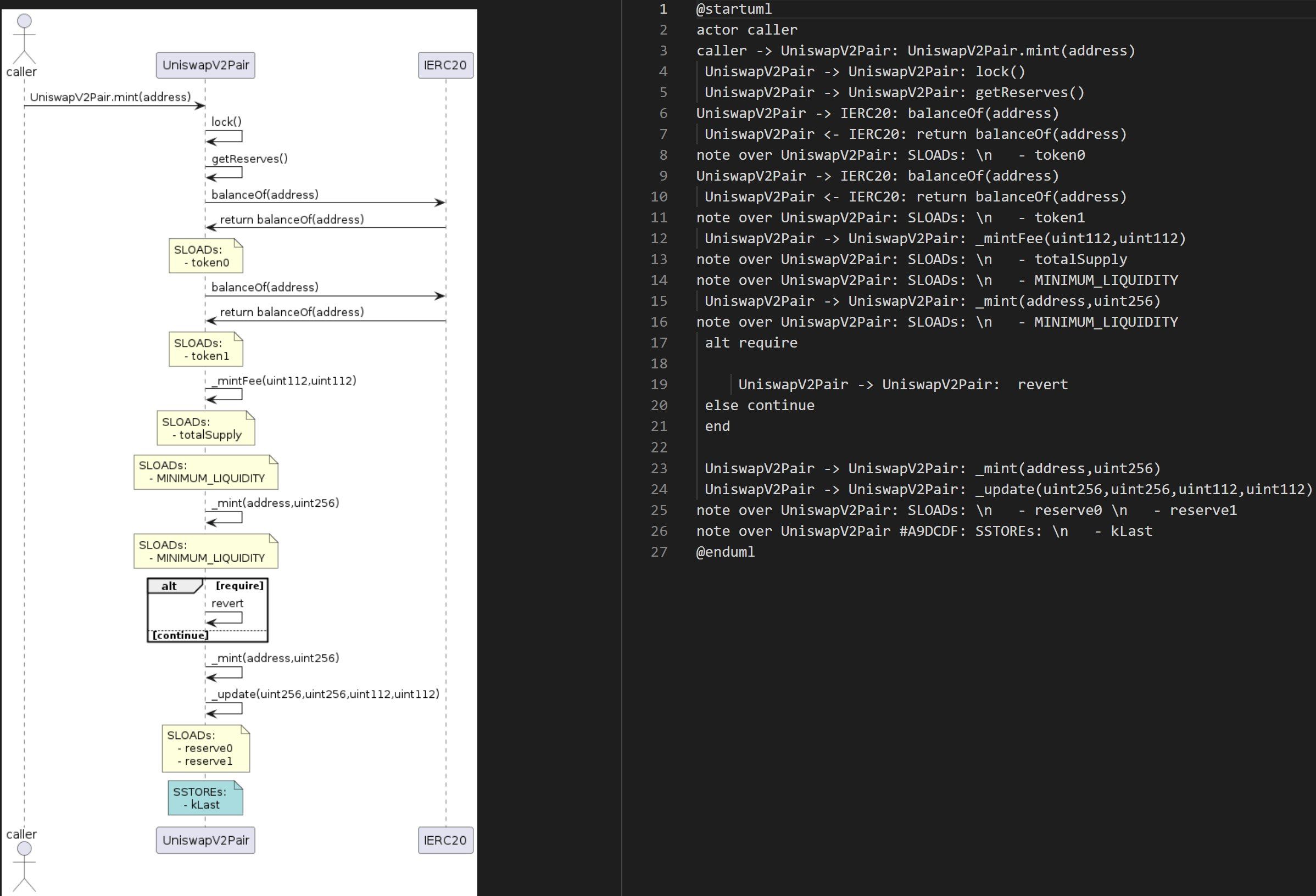
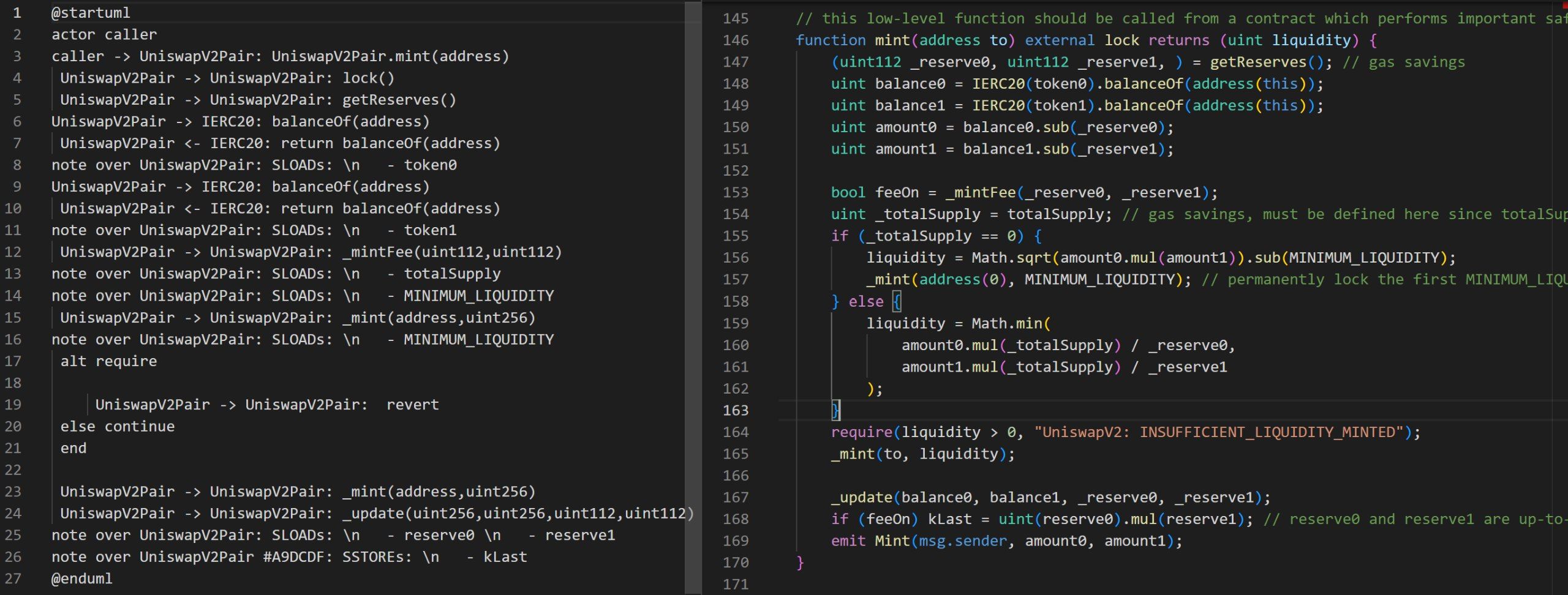
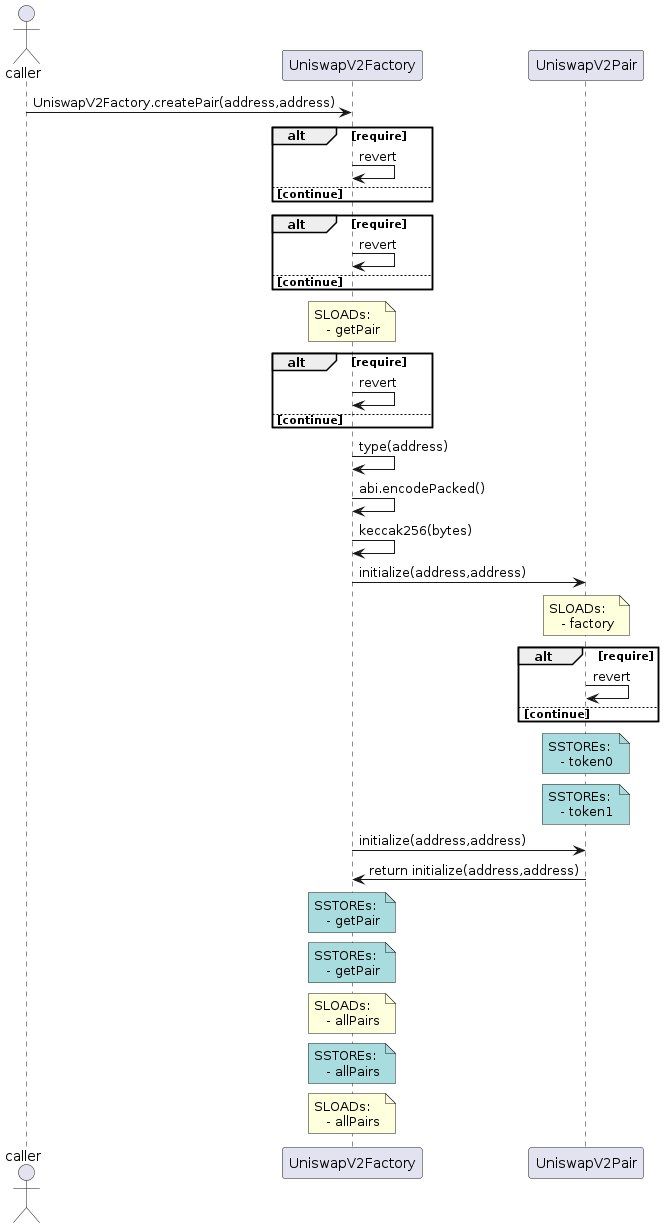
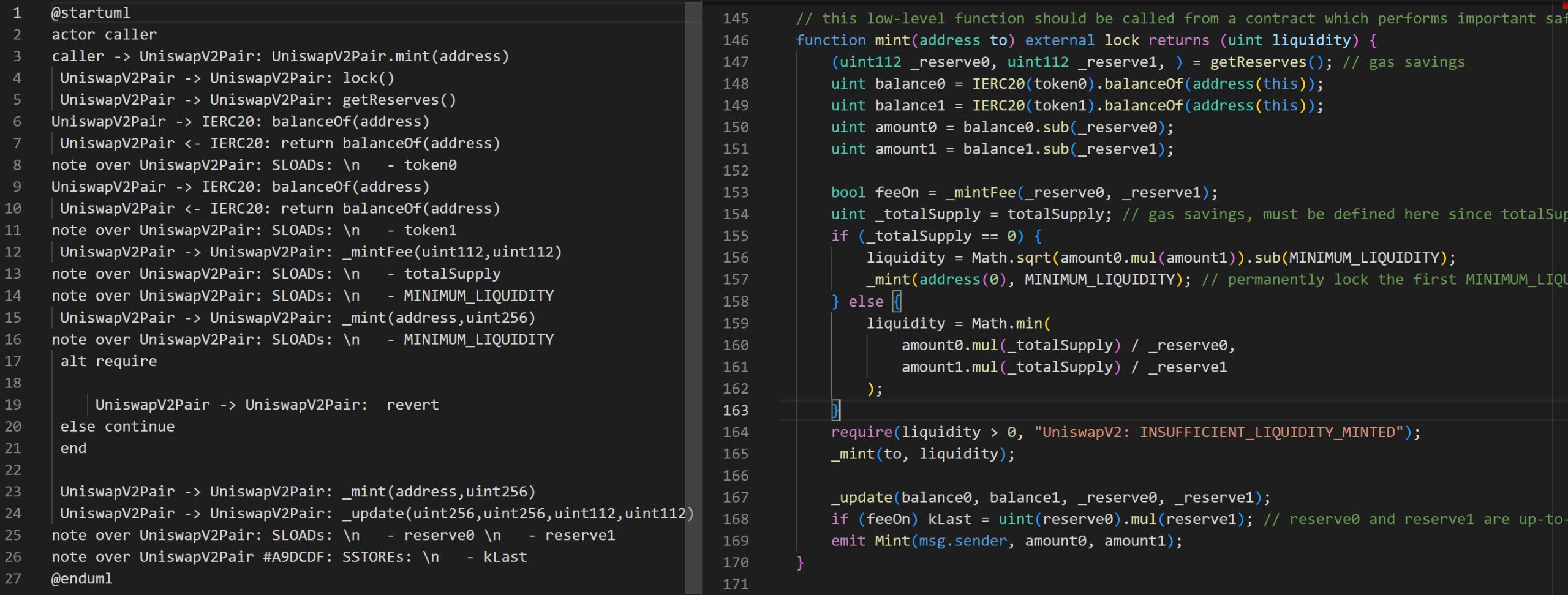
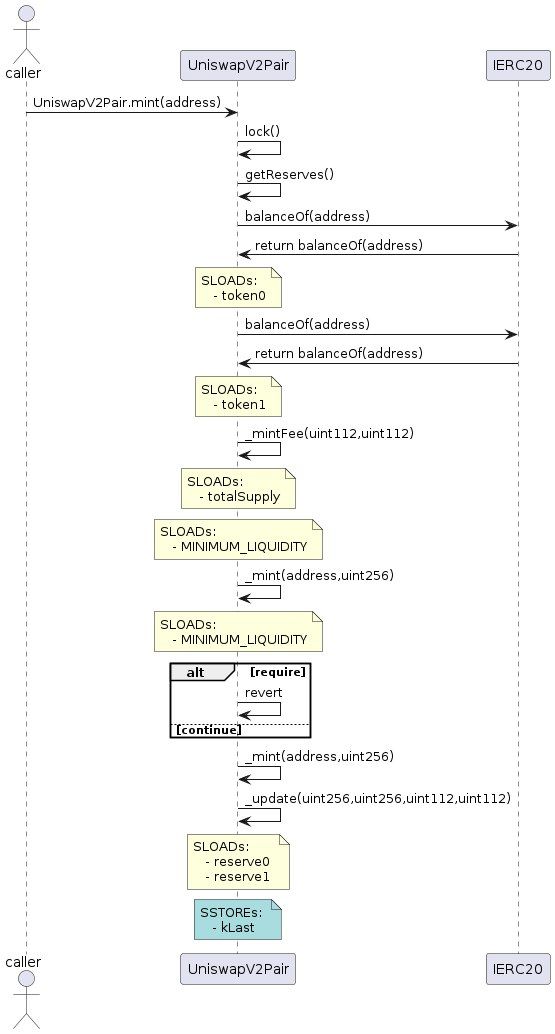
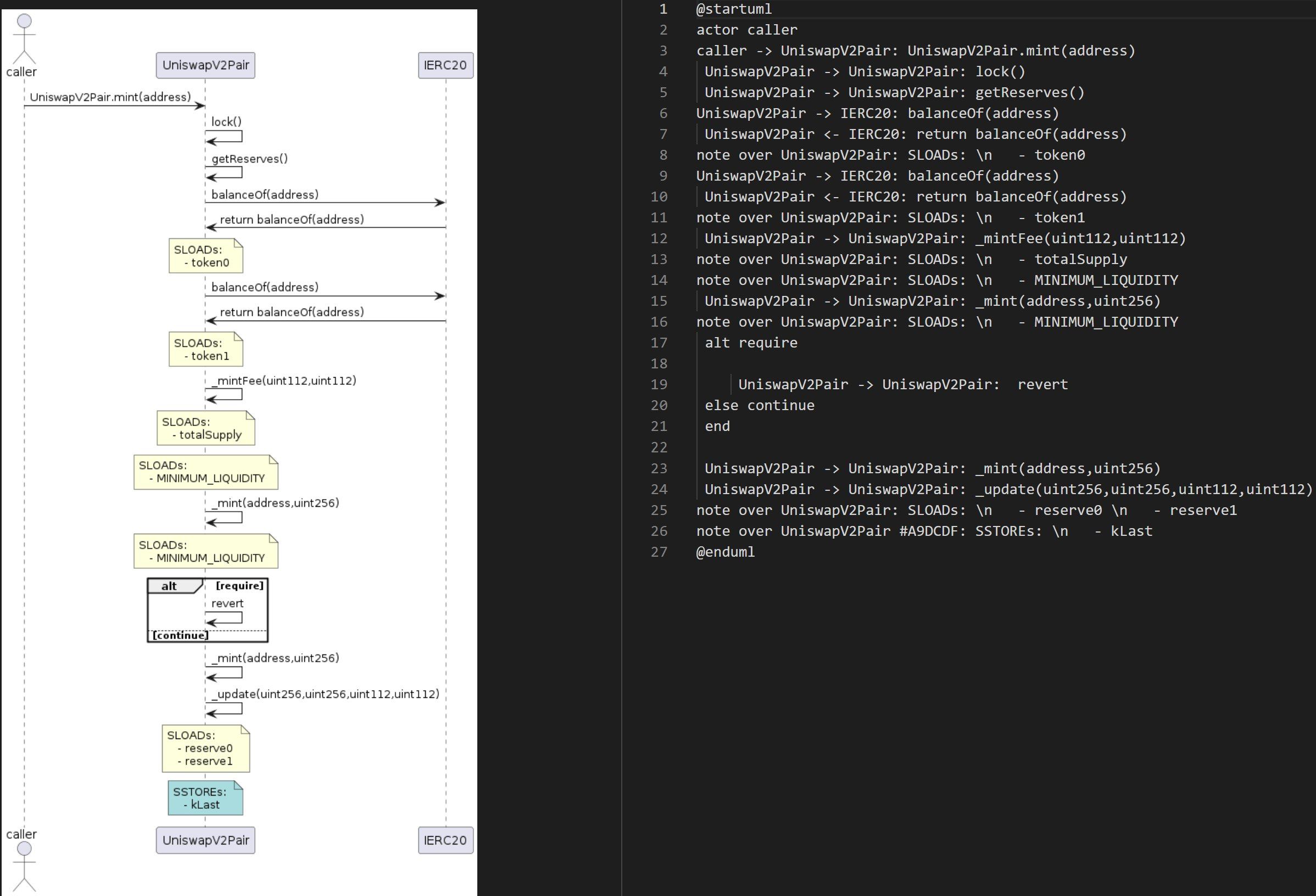
SIREN is a new printer extension on Slither that creates smart contract sequence diagrams with plantUML! As protocols are becoming increasingly complex, they are also becoming more difficult to diagnose for vulnerabilities and critical errors. This issue prompted us to make a tool that produces a visualization of the logic flows for a group of smart contracts.
SIREN is not a protocol design tool, it is a security tool meant for auditing existing code; an ideal use case would be gradual iteration cycling between development and validation, to ensure that projects of any size. Currently, the sequence diagram serves as a visual, human-inspection method, accompanying traditional debugging methods. In the future, developers can build additional functionality in order to add programmatic and more powerful analysis capabilities.
A common concern in protocol development is unnecessary gas consumption, which is tied closely with external function calls. SIREN demonstrates how often cross-contract function calls occur, and the visualization makes it easier to determine, for example, if certain external function call chaining can be shortened. In particular, protocols may have internal function calls that lead into external function calls; these details may be hidden away or difficult to recognize in debugging tools. In contrast, SIREN’s visual representation effectively demonstrates this type of high-level interaction.
How it's Made
We built on top of Slither, an open-source Solidity static analysis framework written in Python. Our solution locates the function of interest as an entry point and then sifts through all paths from there through the codebase. We included custom handling for:
- Conditionals and reverts
- Cross contract calls
- Internal and language level functions
- Storage reads and writes
All relevant intermediate representation (IR) nodes are iterated over and converted into visual representations through plantUML's domain specific language (DSL)
The *.puml files are then processed using the plantUML jar to output analysis ready graphics.
These visuals are vital for spotting several classes of vulnerabilities and errors such as:
- DOS vectors
- Read-only reentrancy occurrences
- Call duplication
- Unnecessary gas consumption
In short, they aid in understanding protocols from a broad perspective.
Throughout the weekend we learned many of Slither's internals and can see new ways to leverage the work Trail of Bits has published.