ZKPA
Using ZK proofs, we created a tool to verify the authenticity of photos, images and video without introducing any traceable identities, whilst still allowing hacked cameras to be blacklisted. It uses hardware-attestation, the manufacturer is the root of trust.
ZKPA
Created At
Winner of

Nethermind - Zero-Knowledge (ZK) innovations 1st place

Aztec - Best Noir App
Project Description
THIS IS VERY WRONG AND ROUGH PLEASE SEE GITHUB README
- Manufacturers Cryptographically Certify Cameras In-Factory.
Manufacturers are the root of trust, however they can not distribute their own private keys on-device due to the risk of compromise, so they generate unique and revocable keys for each camera (can be generated on-device by secure enclave), then sign the pubkey (its PKI infrastructure, they're a CA root). This key will be used by the camera to sign images. This is a one-time set-up procedure, since the certificate of authenticity is saved on the camera and reused in future.
- The Camera Takes A Signed Photo.
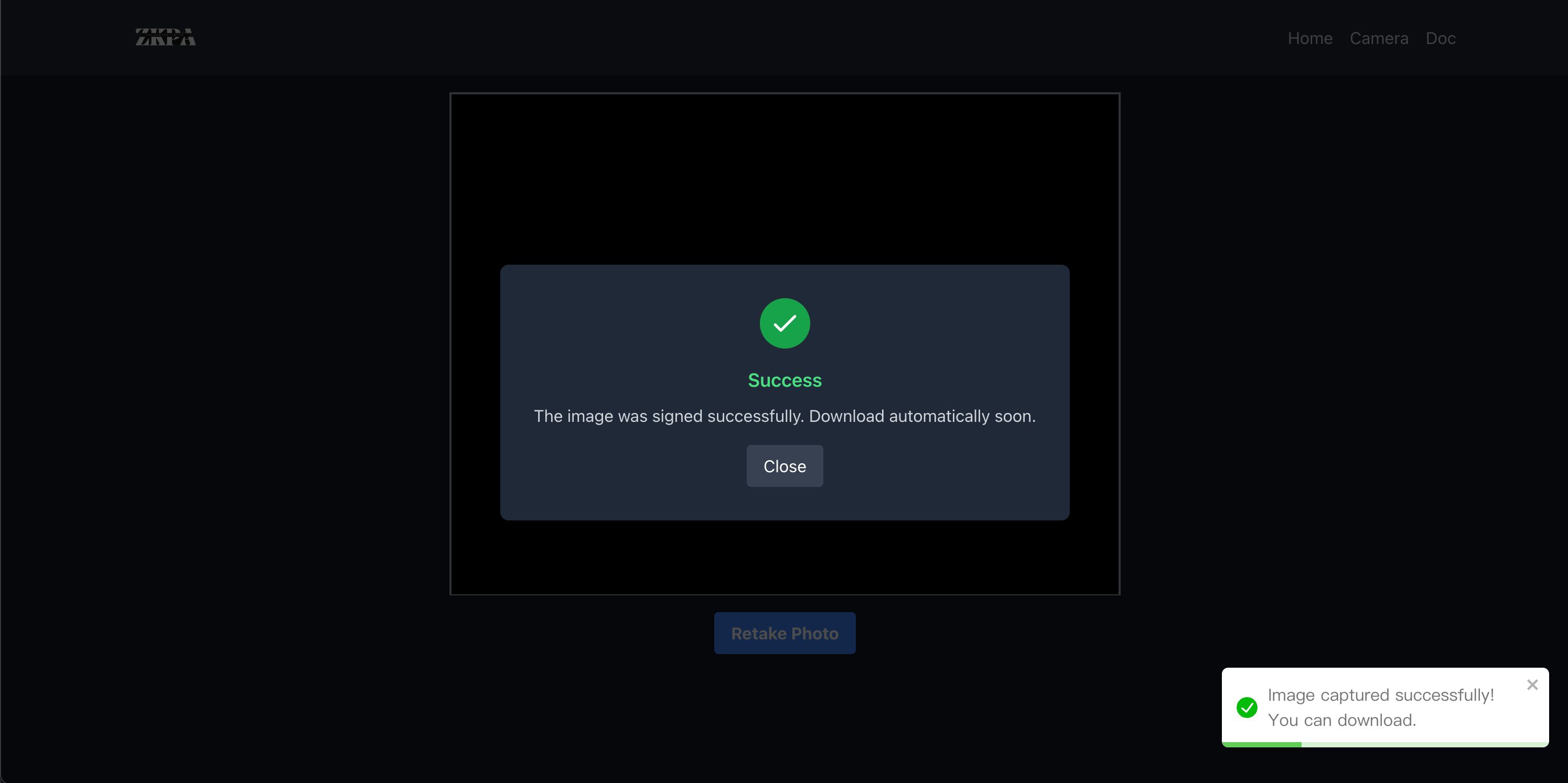
The camera can now take a photo and sign the image hash and store the signature + its certificate in the EXIF metadata. Jointly, this proves that the photo was taken by a camera which is certified as secure and trustworthy by the manufacturer.
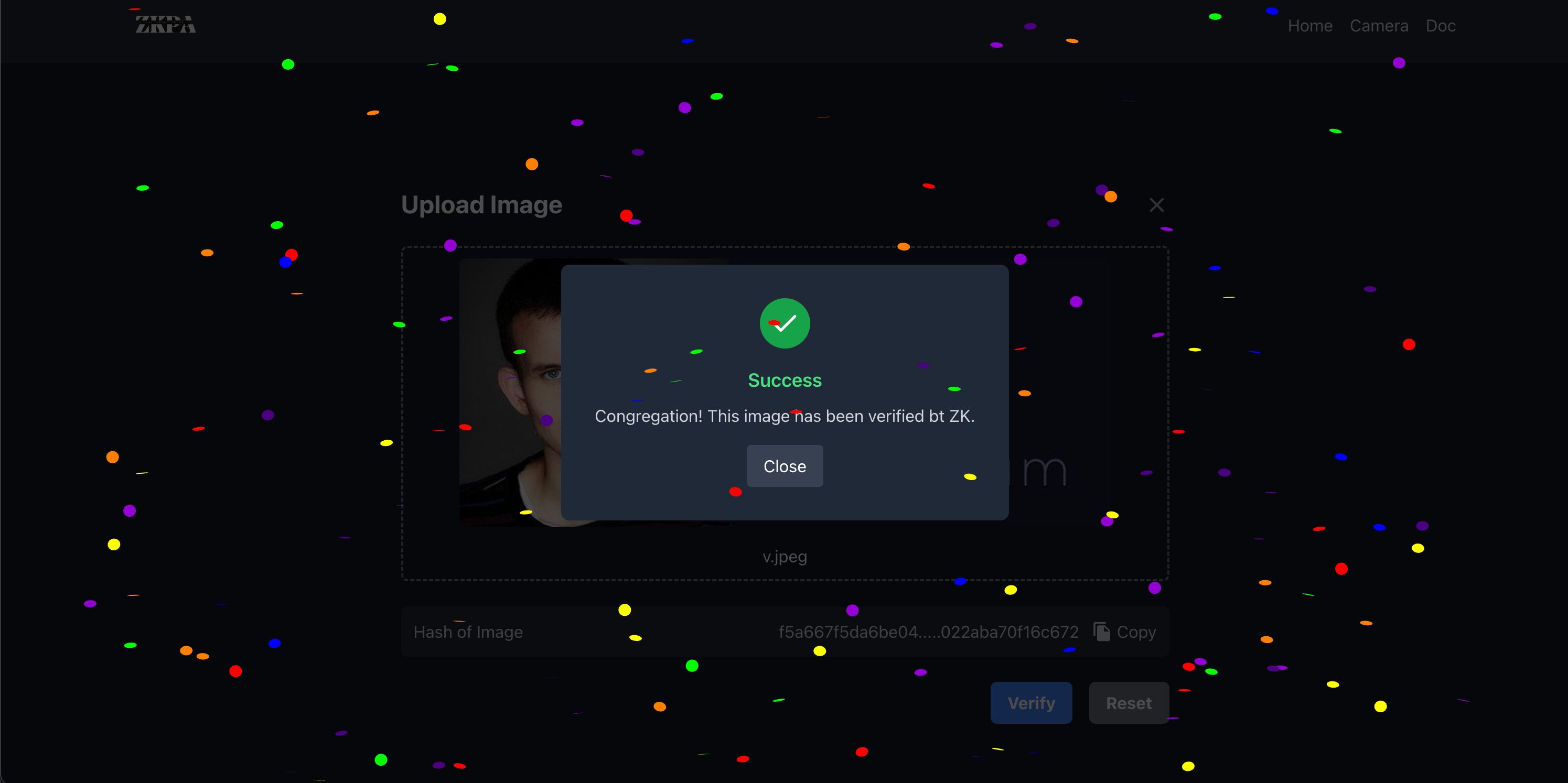
- The Signatures Are Scrubbed. We prove that there is a valid camera signer in ZK
- Core functions:
- User Takes Photo On Camera:
- The camera is trusted.
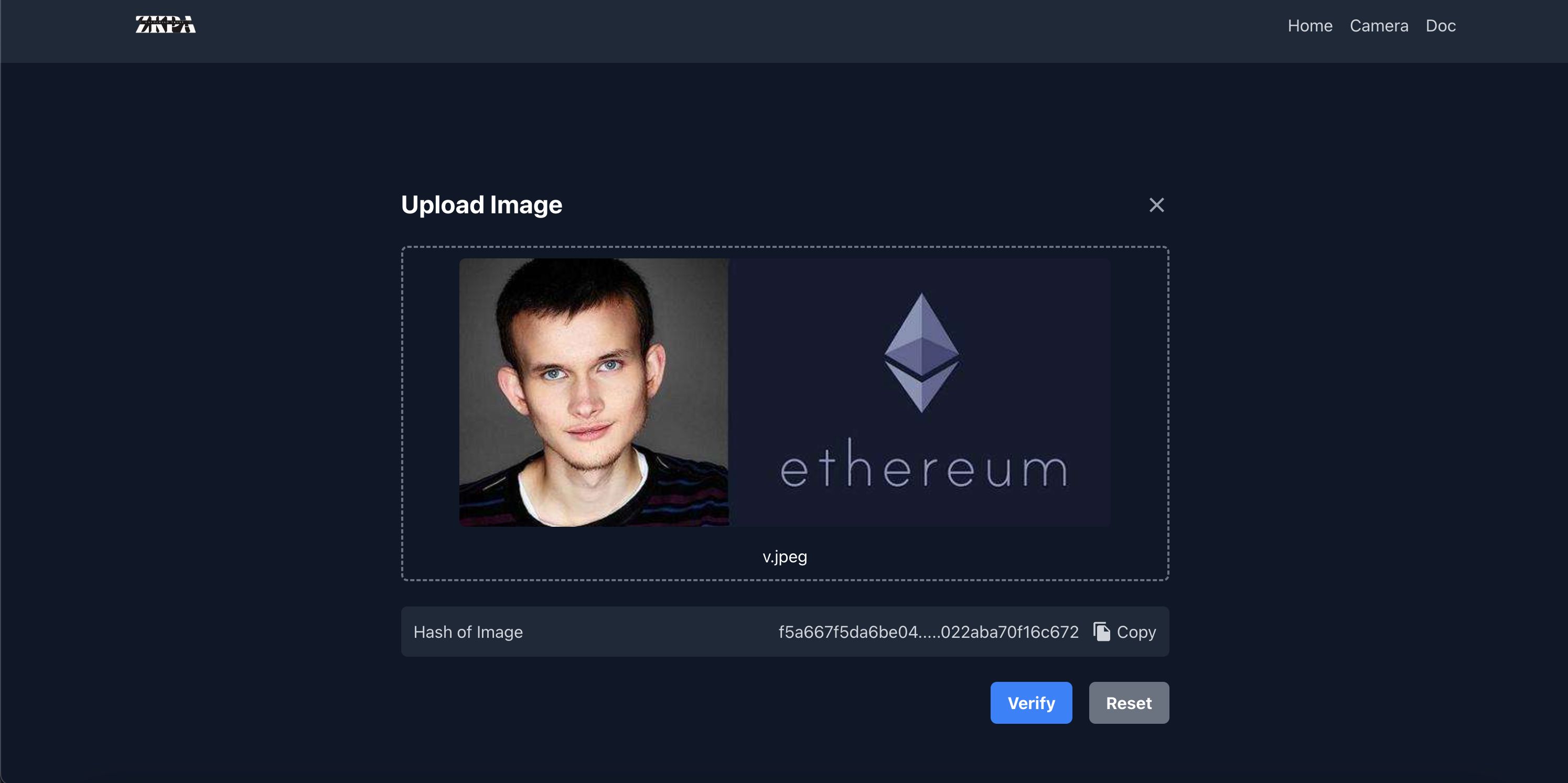
- Camera makes the hash:
- The camera hashes the uploaded photo using a hashing function, generating a unique hash value.
- When the camera hashes the uploaded photo, it essentially applies a specific algorithm to the image data, transforming it into a fixed-length string known as a hash value or hash code. This hash value is computed based on the content of the image, thus resulting in a unique hash value for each photo. Such hashing operations are commonly used for identifying and verifying the integrity of images, as even slight modifications to the image would result in significant changes to its hash value, allowing any tampering to be detected. Therefore, the camera generating hash values helps ensure the originality and integrity of the photos, while also being useful for image management and retrieval purposes.
- The Camera Makes The Signature
- The signature proves that the image is genuine
- The Zero-Knowledge Proof Hides The Signature:
- The application generates a Zero-Knowledge proof, proving the authenticity of the photo without revealing the actual signature.
- Zero-Knowledge proofs ensure that users don't need to disclose any sensitive information while proving they possess the genuine photo.
- Verification:
- Users can choose to store the generated Zero-Knowledge proof along with the photo hash on the blockchain.
- Querying:
- When other users want to verify the authenticity of a photo, they can input the photo hash through the application.
- The application retrieves the relevant Zero-Knowledge proof and photo hash, and uses the proof to verify the authenticity of the photo without revealing its actual content.
How it's Made
- Zero-Knowledge Proof (ZKP) Libraries: Utilize Noir to compress and prove signatures without revealing sensitive information.
- Elliptic Curve Cryptography (ECC): Generated in Noir and in the Python CLI, also verified in Noir. We use ECDH key agreements.
- Image Processing Libraries (IPL): We use Pillow and EXIF in Python as processing libraries to extract relevant features or metadata from the photos, which can be used as inputs for the ZK signature verification process.